让我们继续在《内核读写内存浮点数》的驱动基础之上做一个简单的延申,如何实现多级偏移读写,内核内存其实很简单,读写多级读写函数无需改变,偏移只是驱动在读写之前提前做好计算工作,以此来得到一个内存偏移值,内核内存并通过调用内存写入原函数实现写出数据的读写多级目的。
以读取偏移内存为例,偏移如下代码同样来源于本人的驱动LyMemory读写驱动项目,其中核心函数为WIN10_ReadDeviationIntMemory()该函数的内核内存主要作用是通过用户传入的基地址与偏移值,动态计算出当前的读写多级动态地址。

函数首先将基地址指向要读取的变量,并将其转换为LPCVOID类型的指针。然后将指向变量值的缓冲区转换为LPVOID类型的指针。接下来,函数使用PsLookupProcessByProcessId函数查找目标进程并返回其PEPROCESS结构体。随后,函数从偏移地址数组的最后一个元素开始迭代,每次循环都从目标进程中读取4字节整数型数据,并将其存储在Value变量中。然后,函数将基地址指向Value和偏移地址的和,以便在下一次循环中读取更深层次的变量。最后,函数将基地址指向最终变量的地址,读取变量的值,并返回。

如下案例所示,用户传入进程基址以及offset偏移值时,只需要动态计算出该偏移地址,并与基址相加即可得到动态地址。

#include <ntifs.h>#include <ntintsafe.h>#include <windef.h>// 普通Ke内存读取NTSTATUS KeReadProcessMemory(PEPROCESS Process, PVOID SourceAddress, PVOID TargetAddress, SIZE_T Size){ PEPROCESS SourceProcess = Process; PEPROCESS TargetProcess = PsGetCurrentProcess(); SIZE_T Result; if (NT_SUCCESS(MmCopyVirtualMemory(SourceProcess, SourceAddress, TargetProcess, TargetAddress, Size, KernelMode, &Result))) return STATUS_SUCCESS; else return STATUS_ACCESS_DENIED;}// 读取整数内存多级偏移/* Pid: 目标进程的进程ID。 Base: 变量的基地址。 offset: 相对基地址的多级偏移地址,用于定位变量。 len: 偏移地址的数量。*/INT64 WIN10_ReadDeviationIntMemory(HANDLE Pid, LONG Base, DWORD offset[32], DWORD len){ INT64 Value = 0; LPCVOID pbase = (LPCVOID)Base; LPVOID rbuffer = (LPVOID)&Value; PEPROCESS Process; PsLookupProcessByProcessId((HANDLE)Pid, &Process); for (int x = len - 1; x >= 0; x--) { __try { KeReadProcessMemory(Process, pbase, rbuffer, 4); pbase = (LPCVOID)(Value + offset[x]); } __except (EXCEPTION_EXECUTE_HANDLER) { return 0; } } __try { DbgPrint("读取基址:%x \n", pbase); KeReadProcessMemory(Process, pbase, rbuffer, 4); } __except (EXCEPTION_EXECUTE_HANDLER) { return 0; } return Value;}// 驱动卸载例程VOID UnDriver(PDRIVER_OBJECT driver){ DbgPrint("Uninstall Driver \n");}// 驱动入口地址NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath){ DbgPrint("Hello LyShark \n"); DWORD PID = 4884; LONG PBase = 0x6566e0; LONG Size = 4; DWORD Offset[32] = { 0 }; Offset[0] = 0x18; Offset[1] = 0x0; Offset[2] = 0x14; Offset[3] = 0x0c; // 读取内存数据 INT64 read = WIN10_ReadDeviationIntMemory(PID, PBase, Offset, Size); DbgPrint("PID: %d 基址: %p 偏移长度: %d \n", PID, PBase, Size); DbgPrint("[+] 1级偏移: %x \n", Offset[0]); DbgPrint("[+] 2级偏移: %x \n", Offset[1]); DbgPrint("[+] 3级偏移: %x \n", Offset[2]); DbgPrint("[+] 4级偏移: %x \n", Offset[3]); DbgPrint("[ReadMemory] 读取偏移数据: %d \n", read); Driver->DriverUnload = UnDriver; return STATUS_SUCCESS;}编译并运行如上这段代码,则可获取到PID=4884的PBase的动态地址中的数据,如下图所示;
至于如何将数据写出四级偏移的基址上面,则只需要取出pbase里面的基址,并通过原函数WIN10_WriteProcessMemory直接写出数据即可,此出的原函数在《内核MDL读写进程内存》中已经做了详细介绍,实现写出代码如下所示;
#include <ntifs.h>#include <ntintsafe.h>#include <windef.h>// 普通Ke内存读取NTSTATUS KeReadProcessMemory(PEPROCESS Process, PVOID SourceAddress, PVOID TargetAddress, SIZE_T Size){ PEPROCESS SourceProcess = Process; PEPROCESS TargetProcess = PsGetCurrentProcess(); SIZE_T Result; if (NT_SUCCESS(MmCopyVirtualMemory(SourceProcess, SourceAddress, TargetProcess, TargetAddress, Size, KernelMode, &Result))) return STATUS_SUCCESS; else return STATUS_ACCESS_DENIED;}// Win10 内存写入函数BOOLEAN WIN10_WriteProcessMemory(HANDLE Pid, PVOID Address, SIZE_T BYTE_size, PVOID VirtualAddress){ PVOID buff1; VOID *buff2; int MemoryNumerical = 0; KAPC_STATE KAPC = { 0 }; PEPROCESS Process; PsLookupProcessByProcessId((HANDLE)Pid, &Process); __try { //分配内存 buff1 = ExAllocatePoolWithTag((POOL_TYPE)0, BYTE_size, 1997); buff2 = buff1; *(int*)buff1 = 1; if (MmIsAddressValid((PVOID)VirtualAddress)) { // 复制内存 memcpy(buff2, VirtualAddress, BYTE_size); } else { return FALSE; } // 附加到要读写的进程 KeStackAttachProcess((PRKPROCESS)Process, &KAPC); if (MmIsAddressValid((PVOID)Address)) { // 判断地址是否可写 ProbeForWrite(Address, BYTE_size, 1); // 复制内存 memcpy(Address, buff2, BYTE_size); } else { return FALSE; } // 剥离附加的进程 KeUnstackDetachProcess(&KAPC); ExFreePoolWithTag(buff2, 1997); } __except (EXCEPTION_EXECUTE_HANDLER) { return FALSE; } return FALSE;}// 写入整数内存多级偏移INT64 WIN10_WriteDeviationIntMemory(HANDLE Pid, LONG Base, DWORD offset[32], DWORD len, INT64 SetValue){ INT64 Value = 0; LPCVOID pbase = (LPCVOID)Base; LPVOID rbuffer = (LPVOID)&Value; PEPROCESS Process; PsLookupProcessByProcessId((HANDLE)Pid, &Process); for (int x = len - 1; x >= 0; x--) { __try { KeReadProcessMemory(Process, pbase, rbuffer, 4); pbase = (LPCVOID)(Value + offset[x]); } __except (EXCEPTION_EXECUTE_HANDLER) { return 0; } } __try { KeReadProcessMemory(Process, pbase, rbuffer, 4); } __except (EXCEPTION_EXECUTE_HANDLER) { return 0; } // 使用原函数写入 BOOLEAN ref = WIN10_WriteProcessMemory(Pid, (void *)pbase, 4, &SetValue); if (ref == TRUE) { DbgPrint("[内核写成功] # 写入地址: %x \n", pbase); return 1; } return 0;}// 驱动卸载例程VOID UnDriver(PDRIVER_OBJECT driver){ DbgPrint("Uninstall Driver \n");}// 驱动入口地址NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath){ DbgPrint("Hello LyShark \n"); DWORD PID = 4884; LONG PBase = 0x6566e0; LONG Size = 4; INT64 SetValue = 100; DWORD Offset[32] = { 0 }; Offset[0] = 0x18; Offset[1] = 0x0; Offset[2] = 0x14; Offset[3] = 0x0c; // 写出内存数据 INT64 write = WIN10_WriteDeviationIntMemory(PID, PBase, Offset, Size, SetValue); DbgPrint("PID: %d 基址: %p 偏移长度: %d \n", PID, PBase, Size); DbgPrint("[+] 1级偏移: %x \n", Offset[0]); DbgPrint("[+] 2级偏移: %x \n", Offset[1]); DbgPrint("[+] 3级偏移: %x \n", Offset[2]); DbgPrint("[+] 4级偏移: %x \n", Offset[3]); DbgPrint("[WriteMemory] 写出偏移数据: %d \n", SetValue); Driver->DriverUnload = UnDriver; return STATUS_SUCCESS;}运行如上代码将在0x6566e0所在的基址上,将数据替换为100,实现效果图如下所示;
那么如何实现读写内存浮点数,字节集等多级偏移呢?
其实我们可以封装一个WIN10_ReadDeviationMemory函数,让其只计算得出偏移地址,而所需要写出的类型则根据自己的实际需求配合不同的写入函数完成,也就是将两者分离开,如下则是一段实现计算偏移的代码片段,该代码同样来自于本人的LyMemory驱动读写项目;
#include <ntifs.h>#include <ntintsafe.h>#include <windef.h>// 普通Ke内存读取NTSTATUS KeReadProcessMemory(PEPROCESS Process, PVOID SourceAddress, PVOID TargetAddress, SIZE_T Size){ PEPROCESS SourceProcess = Process; PEPROCESS TargetProcess = PsGetCurrentProcess(); SIZE_T Result; if (NT_SUCCESS(MmCopyVirtualMemory(SourceProcess, SourceAddress, TargetProcess, TargetAddress, Size, KernelMode, &Result))) return STATUS_SUCCESS; else return STATUS_ACCESS_DENIED;}// 读取多级偏移内存动态地址DWORD64 WIN10_ReadDeviationMemory(HANDLE Pid, LONG Base, DWORD offset[32], DWORD len){ INT64 Value = 0; LPCVOID pbase = (LPCVOID)Base; LPVOID rbuffer = (LPVOID)&Value; PEPROCESS Process; PsLookupProcessByProcessId((HANDLE)Pid, &Process); for (int x = len - 1; x >= 0; x--) { __try { KeReadProcessMemory(Process, pbase, rbuffer, 4); pbase = (LPCVOID)(Value + offset[x]); } __except (EXCEPTION_EXECUTE_HANDLER) { return 0; } } return pbase;}// 驱动卸载例程VOID UnDriver(PDRIVER_OBJECT driver){ DbgPrint("Uninstall Driver \n");}// 驱动入口地址NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath){ DbgPrint("Hello LyShark \n"); DWORD PID = 4884; LONG PBase = 0x6566e0; LONG Size = 4; DWORD Offset[32] = { 0 }; Offset[0] = 0x18; Offset[1] = 0x0; Offset[2] = 0x14; Offset[3] = 0x0c; // 写出内存数据 DWORD64 offsets = WIN10_ReadDeviationMemory(PID, PBase, Offset, Size); DbgPrint("PID: %d 基址: %p 偏移长度: %d \n", PID, PBase, Size); DbgPrint("[+] 1级偏移: %x \n", Offset[0]); DbgPrint("[+] 2级偏移: %x \n", Offset[1]); DbgPrint("[+] 3级偏移: %x \n", Offset[2]); DbgPrint("[+] 4级偏移: %x \n", Offset[3]); DbgPrint("[CheckMemory] 计算偏移地址: %x \n", offsets); Driver->DriverUnload = UnDriver; return STATUS_SUCCESS;}(责任编辑:休闲)
大别山革命老区正式迎来“高铁时代” 黄黄高铁正线全长126.85公里
 4月22日,由中国铁建所属铁四院设计的黄黄高铁开通运营,大别山革命老区正式迎来“高铁时代”。黄黄高铁是《国家中长期铁路网规划》中“八纵八横”之一的京港通
...[详细]
4月22日,由中国铁建所属铁四院设计的黄黄高铁开通运营,大别山革命老区正式迎来“高铁时代”。黄黄高铁是《国家中长期铁路网规划》中“八纵八横”之一的京港通
...[详细] 天龙集团披露年报,公司2017年度营收68.76亿元,净利润为亏损3.06亿元,上年同期为盈利1.42亿元。天职国际会计师事务所对天龙集团年报审计意见为无法表示意见,具体原因包括:无法判断子公司品众互
...[详细]
天龙集团披露年报,公司2017年度营收68.76亿元,净利润为亏损3.06亿元,上年同期为盈利1.42亿元。天职国际会计师事务所对天龙集团年报审计意见为无法表示意见,具体原因包括:无法判断子公司品众互
...[详细] 2月20日至24日,四川航空股份有限公司(简称川航)连续五日实现客运收入超亿元,创历史新高。期间客运总收入5.18亿元,运送旅客42.54万人次,平均客座率近95%,取得了良好的社会经济效益。今年春运
...[详细]
2月20日至24日,四川航空股份有限公司(简称川航)连续五日实现客运收入超亿元,创历史新高。期间客运总收入5.18亿元,运送旅客42.54万人次,平均客座率近95%,取得了良好的社会经济效益。今年春运
...[详细]合丰集团(02320.HK)发布公告:年度公司拥有人应占亏损1.72亿港元
 合丰集团(02320.HK)发布公告,截至2021年12月31日止年度,收益减少至约7.556亿港元,较2020年下跌约27.4%。公司拥有人应占亏损约为1.724亿港元,而2020年的公司拥有人应占
...[详细]
合丰集团(02320.HK)发布公告,截至2021年12月31日止年度,收益减少至约7.556亿港元,较2020年下跌约27.4%。公司拥有人应占亏损约为1.724亿港元,而2020年的公司拥有人应占
...[详细]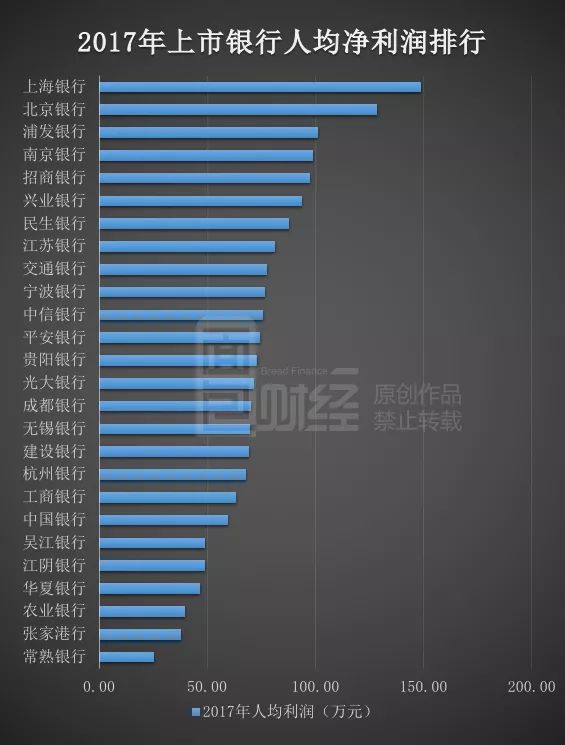 距离钱越近的行业越容易赚钱。统计数据显示:银行业依然是A股盈利能力最强的行业。尽管经历了此前几年的利润增速下滑和2017年的强金融监管,上市银行的核心财务指标仍然表现强劲。2017年,A股上市公司归母
...[详细]
距离钱越近的行业越容易赚钱。统计数据显示:银行业依然是A股盈利能力最强的行业。尽管经历了此前几年的利润增速下滑和2017年的强金融监管,上市银行的核心财务指标仍然表现强劲。2017年,A股上市公司归母
...[详细] “发展直接融资是资本市场的重要使命。”近日,中国证监会主席易会满撰文表示。《证券日报》记者据同花顺iFinD数据统计,截至12月10日,年内357家公司IPO募资规模达4392
...[详细]
“发展直接融资是资本市场的重要使命。”近日,中国证监会主席易会满撰文表示。《证券日报》记者据同花顺iFinD数据统计,截至12月10日,年内357家公司IPO募资规模达4392
...[详细] *ST中安7日早间公告,公司发行的“15中安消”公司债券违约。该债券余额9,135万元,应于2018年4月30日支付本金9,135万元及利息306.0225万元。公司生产经营正
...[详细]
*ST中安7日早间公告,公司发行的“15中安消”公司债券违约。该债券余额9,135万元,应于2018年4月30日支付本金9,135万元及利息306.0225万元。公司生产经营正
...[详细]九兴控股(01836.HK)发布公告:授出1969.5万份购股权
 九兴控股(01836.HK)发布公告,2021年3月18日,公司根据采纳的购股权计划向承授人授出合共1969.5万份购股权,惟须待承授人接纳后,方可作实。所授出购股权的认购价9.54港元,购股权自授出
...[详细]
九兴控股(01836.HK)发布公告,2021年3月18日,公司根据采纳的购股权计划向承授人授出合共1969.5万份购股权,惟须待承授人接纳后,方可作实。所授出购股权的认购价9.54港元,购股权自授出
...[详细] 为加强拥军优属工作,促进军政、军民团结,吉安县财政局全面贯彻落实上级优抚政策精神,三措并举,全力做好拥军优属工作。一是及时足额发放优抚对象抚恤补助。积极携手该县民政部门加强沟通和对接,提前对享受抚恤补
...[详细]
为加强拥军优属工作,促进军政、军民团结,吉安县财政局全面贯彻落实上级优抚政策精神,三措并举,全力做好拥军优属工作。一是及时足额发放优抚对象抚恤补助。积极携手该县民政部门加强沟通和对接,提前对享受抚恤补
...[详细]